Be default, intranet users are authenticated using the password stored by the
MySQL database. Intranet user accounts can also authenticated via LDAP. This
means that users can be autheticated via Windows Active Directory (2000 and
2003 server) , Open LDAP, Kero Mail server and so on. This is set on a per user
basis by the Intranet administrator. This does require that PHP has the ldap
extension compiled or enabled.
The administrative user has access to a link called Intranet Administration. Click on this.

Click on User accounts.
Click on the Edit link beside the user account you want to modify.
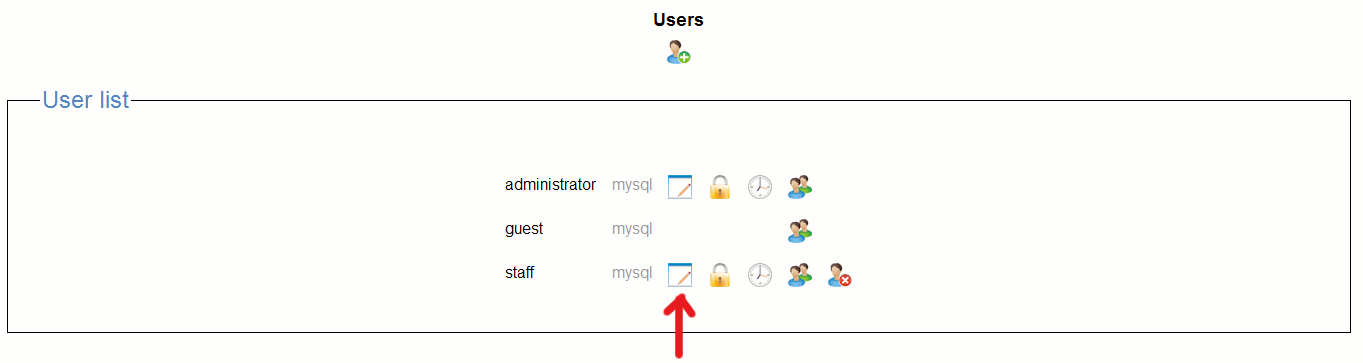
Change authentication method to active diretory or Openldap.
Below this enter the ldap DN (distinguashed name). In the case of the Active
directory it can also be the windows domain user name.
Examples:
fred.frog@foo.org
CN=fred frog,CN=Users,DC=foo,DC=org
(this format must be used if you want users to be able to update their windows
password)
To find the exact syntax you can use the LDIFDE Active Directory tool to see
the Windows LDAP schema.
Edit the Intranet config file includes/config.php
//LDAP SETTINGS
//ldap server
$LDAPHOST = "ldapserverip";
//ldap domain
//windows domain name
$LDAPDOMAIN = "foo.org";
//allow updates to passwords on ldap (windows) server
$LDAPUPDATE = "yes";
//ldap administrative account user name - only needed if wanting to change active
directory password
$LDAPADMINDN = "cn=Administrator,cn=Users,dc=foo,dc=org";
//ldap administrative account password - only needed if wanting to change active
directory password
$LDAPADMINPASS = "administratorpassword";
For read only authentication the only paremeter "LDAPHOST" is necessary.
If you want to be able to force users to update their windows password via the intranet, then the further parameters are necessary.
$LDAPUPDATE = "yes";
$LDAPADMINDN must be set the ldap distinguashed name of an administrator account.
$LDAPADMINPASS must be set to password of above account.
The default port number for ldap is 389. To be able to update windows active directory, the intranet server must connect to the windows domain controller on a secure ldap/ssl tcp port 636.
One way of doing this is to install stunnel (http://www.stunnel.org/) on the intranet server. This will listen for ldap connections (port 389) and redirect them as a ldaps secure (port 636) connections to the ldap server (windows domain controller)
.
To do this
1) Install openssl and stunnel
2) the ldap server name in intranet prefrences would look like this ldap://127.0.0.1/
(ldap connections sent to localhost).
3) edit stunnel.conf it to look like the following. Replace "ldapserver"
with the ip address of the ldap server.
client = yes
verify = 0
; Service-level configuration
[ldap]
accept = 127.0.0.1:389
connect = ldapserver:636
Make sure that hostname or ip used in accept parameter is the same as that used for $LDAPHOST in config.php.
Make sure that the you use the hostname not an ip address in the connect parameter.
Before Active directory will acept secure ldap connections, a certificate needs to installed.
Install certificate services (The installation CD is needed)
1. Open Control Panel and select Add/Remove Programs.
2. Choose Add/Remove Windows Components.
3. Select Certificate Services, then click Next.
4. Select Enterprise root CA, then click Next.
5. Fill in CA identifying information and click Next.
.
Create certificate
1. Install an Enterprise Certificate Authority on a Windows 2000 Domain Controller,
which installs a certificate on a server or install a third-party certificate
on the Domain Controller.
2. Click Start>All Programs>Administrative Tools>Active Directory Users
and Computer.
3. In the Active Directory Users and Computers window, right-click on your domain
name and select Properties.
4. In the Domain Properties dialog box, select the Group Policy tab.
5. Select the Default Domain Policy group policy and then click Edit.
6. Select Windows Settings under Computer Configuration.
7. Select Security Settings and then select Public Key Policies.
8. Select Automatic Certificate Request Settings.
9. Use the wizard to add a policy for Domain Controllers.
Verify that SSL has been enabled on the server. You can do this by using the ldp.exe tool. This can be obtained by installing suptools.msi from Windows installation cd's \Support\tools directory onto a client PC.
Run the command Start > Run > "ldp"
Connect and supply valid hostname of the domain controller and port number 636.
Also select the SSL check box. If you can connect, that means that the domain controller has been setup to accept secure ldap connections.